Emulating Hypervisors: a Samsung RKP case study (OffensiveCon 2020)
Hello, I'm Aris Thallas, a computer security researcher working at CENSUS. Back in February 2020 I had the pleasure of presenting my work on proprietary hypervisor emulation and bug discovery at the OffensiveCon 2020 conference.
Besides their common use for system virtualization, hypervisors have been adopted in the Android ecosystem as a kernel protection against runtime attacks. Each OEM/vendor is free to implement their own hypervisors by employing the ARM virtualization extensions. Due to the lack of proper debugging and system inspection support in the Android ecosystem in general such implementations have been extremely difficult to audit/reverse/debug. This situation has been further complicated by OEMs/vendors failing to release documentation, source code, tools, etc. for these components publicly.
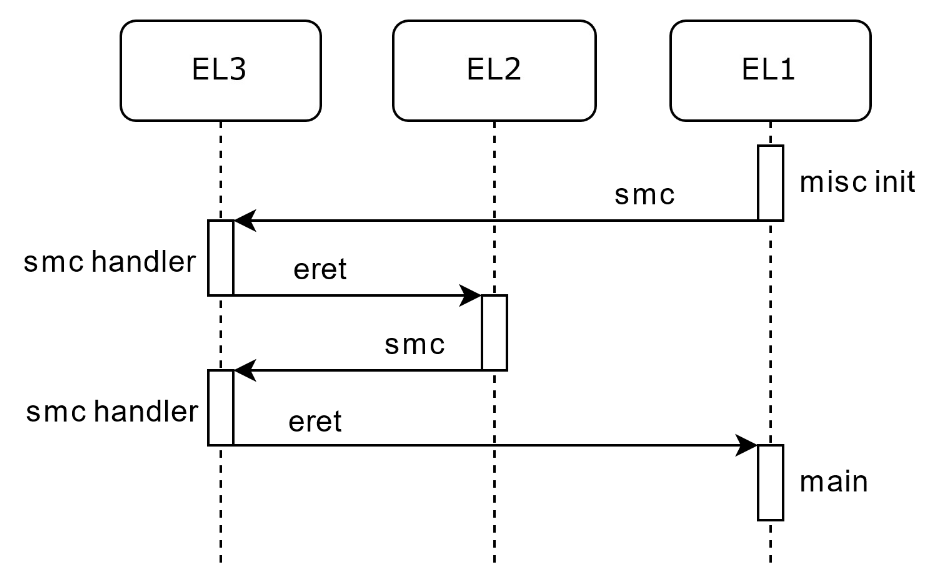
The OffensiveCon 2020 presentation entitled "Emulating Hypervisors; a Samsung RKP case study" focused on the emulation of proprietary hypervisors under QEMU which provides users full control over the emulated system, including debugging capabilities. The presentation discussed ARM system development and virtualization extension topics, laying the foundations for arbitrary hypervisor debugging work on ARM architectures. Examples were showcased through a custom framework that allowed for bootstraping and interacting with the Samsung S8 proprietary hypervisor. The presentation concluded with a demonstration of fuzzing capabilities that were made possible through the framework.
You may find the related presentation material below:
I would like to thank the organizers of OffensiveCon 2020 for an excellent conference!
